Artificial Intelligence (AI) is the hot topic with AI Search and Generative Engine Optimization (GEO) has flooded the marketplace. According to a Semrush study, that means the content composition and structure elements are showing strong correlations to visibility and AI citations.
Just as was seen in Search Engine Optimization (SEO), the field is not stagnant. The way these engines review and evaluate content is evolving. Not only is it impacted by the way users search, but the way providers are posting and managing content.
We are in a world with a new competitive landscape where the metric of success is no longer just page ranking or keyword position, but a citation. If your brand isn’t being referenced in an AI-generated response, it simply doesn’t exist in that moment of discovery. Presence has replaced position.
So, at this point in time, what are the things that will ensure the content you write helps you build authority and gets citations in AI responses. SEMRush did an AI content research study that looked at 15,000 AI responses and 60,00 Search Engine Results Pages (SERPS) to determine content qualities that showed a positive correlation and what showed a negative correlation. Those elements are:
- Clarity and summarization: +32.83%
- EEAT signals: +30.64%
- Q&A format: +25.45%
- Section structure: +22.91%
- Structured data elements: +21.60%
- Non-promotional tone: -26.19%
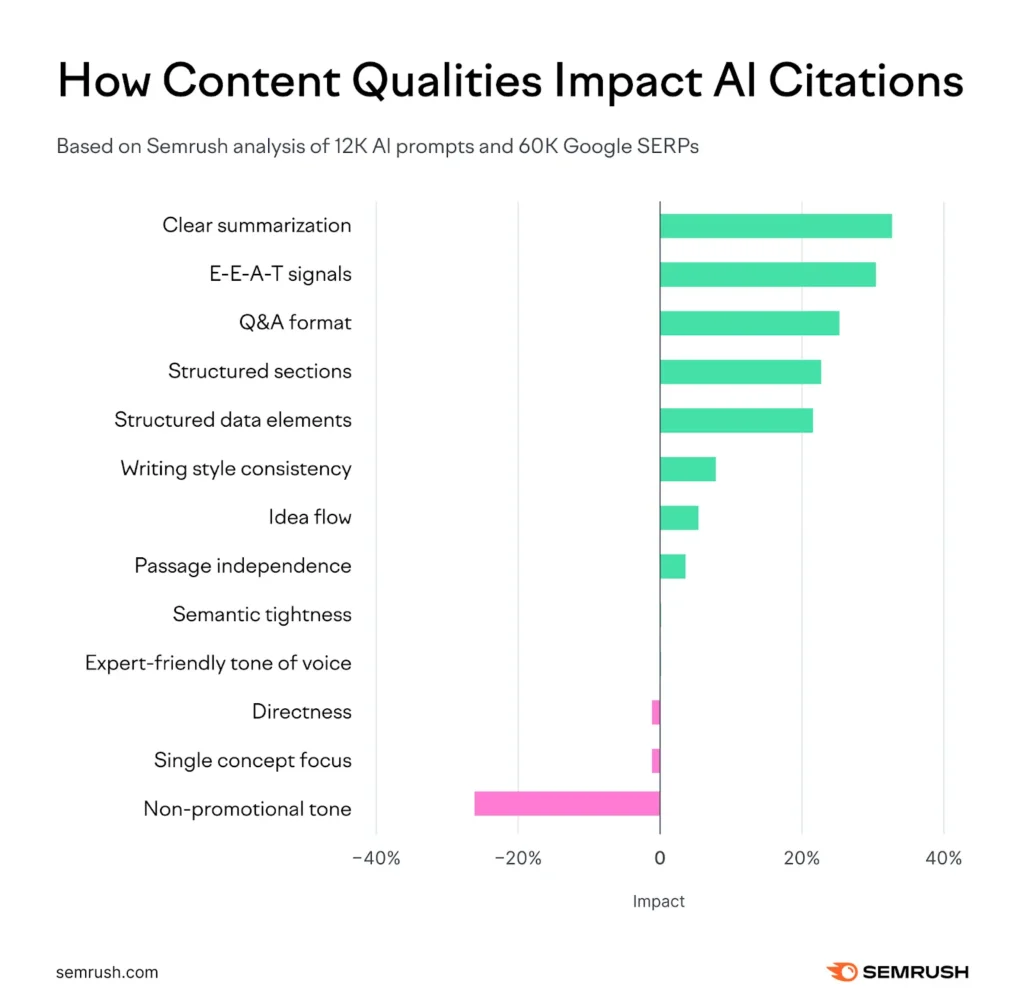
If we only look at the top elements, the study results show that content providing clear answers, demonstrating expertise, and using structured formatting will get cited more often.
AI Content Quality Definitions
It seems simple enough, but what does all of that mean?
In the chart below, SEMrush breaks down what each of the parameters of the study means. It is worth looking at two of these elements more in depth: clear summarization and non-promotional tone.
For clear summarization, it helps to reinforce that the opening of the content provides a summary of what is in the content. This could be in the form of an outline of what is below, providing an answer for the question in the first paragraph and giving a key takeaway.
According to Cecelia Meis, Senior Editor at SEMrush, “Clarity and structure are not SEO shortcuts. They simply make information easier for both people and AI systems to interpret. When content is organized, direct, and backed by clear expertise, models can understand it more reliably.“
When I think about this, what is AI trying to do? It is not only to prompt thoughtful and well-written content. I am thinking they are also devaluing content that is meant to be click bait. For example, when an article starts with a flashy headline and waits until you scroll through the whole article or cycle through several pages to give you an answer.
If you ask AI a question, it wants to provide an answer it finds trustworthy (part of the EEAT signals). If you try to bury the answer WAY down the page, that style of content will not be considered authoritative, but rather being classified as clickbait or spam.
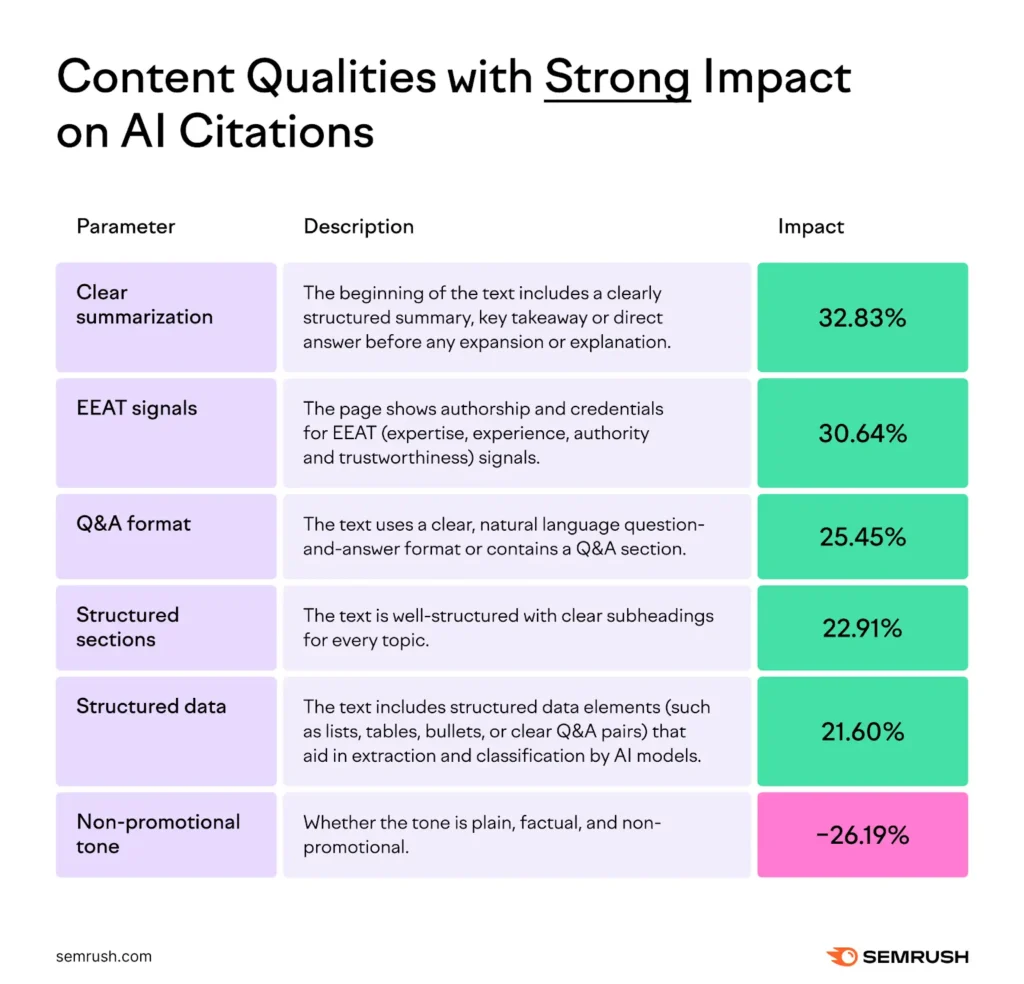
The second elements to really consider is the one that had a negative correlations – Non-promotional tone.
According the SEMRush study, “non-promotional tone, which showed a negative correlation. This doesn’t necessarily mean LLMs prefer promotional language. A more likely explanation is that professionally written articles, which tend to be well-structured, well-sourced, and optimized, often use a commercial or persuasive tone. “
Putting the Findings into Action
Now that you can see some of the results of what impacts AI citations, what can you do?
An easy way to get start is to do an experiment with your content to improve your AI visibility.
Stary by looking for pages that ranking well on traditional Google SERPS but perform poorly in AI search. If you use the criteria for top citations, how do those article compare?
If you use SEMRush, check your top ranking pages with the Organic Rankings Positions report, and your top AI cited pages with the Visibility Overview report.
You can update those pages with author credentials, adding links to reliable sources, update formatting to include Q&A sections where readers benefit from direct answers and review the structure with headings, lists, tables, or charts. All of these elements will help LLMs segment the content.
Next Steps
If setting up and running a study seems overwhelming or if you don’t have access to SEMrush or other AI / Search tools, Digital Insight Labs can help. We would be more than happy to work with your team to support any AI efforts and help evaluation how you are performing in AI.